Oracle7 Server Concepts






Types of Integrity Constraints
The integrity constraints that you can use to impose restrictions on the input of column values can be of the following types:
The following sections explain each type of integrity constraint in detail. The information in each section includes the following:
- the rule enforced by the constraint
- an example of the constraint
- recommendations for appropriate use of the constraint
- other important information about the constraint
NOT NULL Integrity Constraints
By default, all columns in a table allow nulls (the absence of a value). A NOT NULL constraint requires that no nulls be allowed in a column of a table. For example, you can define a NOT NULL constraint to require that a value be input in the ENAME column for every row of the EMP table.
Figure 7 - 2 illustrates a NOT NULL integrity constraint.
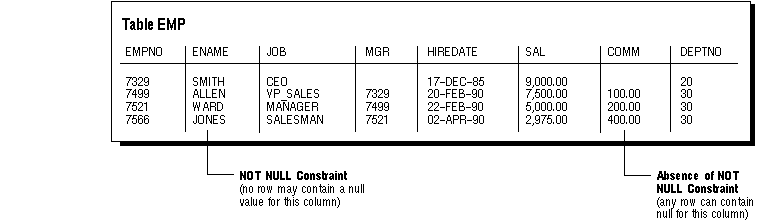
Figure 7 - 2. NOT NULL Integrity Constraints
UNIQUE Key Integrity Constraints
A UNIQUE key integrity constraint requires that no two rows of a table have duplicate values in a specified column or set of columns.
For example, consider the DEPT table in Figure 7 - 3. A UNIQUE key constraint is defined on the DNAME column to disallow rows with duplicate department names.
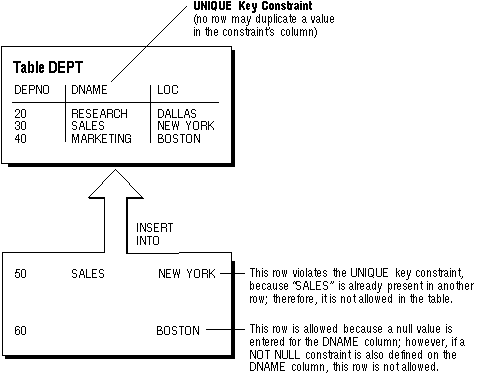
Figure 7 - 3. A UNIQUE Key Constraint
Unique Keys
The column (or set of columns) included in the definition of the UNIQUE key constraint is called the unique key. The term "unique key" is often incorrectly used as a synonym for the terms "UNIQUE key constraint" or "UNIQUE index"; however, note that the term "key" refers only to the list of columns used in the definition of the integrity constraint.
If the UNIQUE key constraint is comprised of more than one column, that group of columns is said to be a composite unique key. For example, in Figure 7 - 4, the CUSTOMER table has a UNIQUE key constraint defined on the composite unique key: the AREA and PHONE columns.
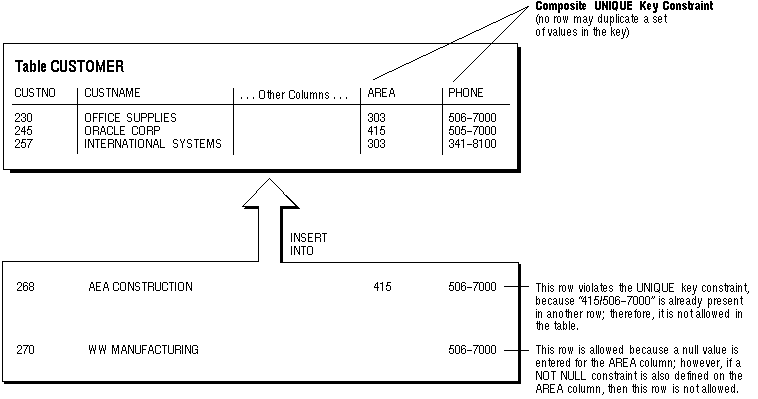
Figure 7 - 4. A Composite UNIQUE Key Constraint
This UNIQUE key constraint allows you to enter an area code and phone number any number of times, but the combination of a given area code and given phone number cannot be duplicated in the table. This eliminates unintentional duplication of a phone number.
UNIQUE Key Constraints and Indexes
Oracle enforces unique integrity constraints with indexes. In Figure 7 - 4, Oracle enforces the UNIQUE key constraint by implicitly creating a unique index on the composite unique key. Because Oracle enforces UNIQUE key constraints using indexes, composite UNIQUE key constraints are limited to the same limitations imposed on composite indexes: up to 16 columns can constitute a composite unique key, and the total size (in bytes) of a key value cannot exceed approximately half the associated database's block size.
Combining UNIQUE Key and NOT NULL Integrity Constraints
Notice in the examples of the previous section that UNIQUE key constraints allow the input of nulls unless you also define NOT NULL constraints for the same columns. In fact, any number of rows can include nulls for columns without NOT NULL constraints because nulls are not considered equal. A null in a column (or in all columns of a composite UNIQUE key) always satisfies a UNIQUE key constraint.
It is common to define unique keys on columns with NOT NULL integrity constraints. This combination forces the user to input values in the unique key; this combination of data integrity rules eliminates the possibility that any new row's data will ever risk conflicting with an existing row's data.
Note: Because of the search mechanism for UNIQUE constraints on more than one column, you cannot have identical values in the non-null columns of a partially null composite UNIQUE key constraint.
PRIMARY KEY Integrity Constraints
Each table in the database can have at most one PRIMARY KEY constraint. The values in the group of one or more columns subject to this constraint constitute the unique identifier of the row. In effect, each row is named by its primary key values.
The Oracle implementation of the PRIMARY KEY integrity constraint guarantees that both of the following are true:
- No two rows of a table have duplicate values in the specified column or set of columns.
- The primary key columns do not allow nulls (that is, a value must exist for the primary key columns in each row).
Primary Keys
The column (or set of columns) included in the definition of a table's PRIMARY KEY integrity constraint is called the primary key. Although it is not required, every table should have a primary key so that
- each row in the table can be uniquely identified
- no duplicate rows exist in the table
Figure 7 - 5 illustrates a PRIMARY KEY constraint in the DEPT table and examples of rows that the constraint prevents from entering the table.
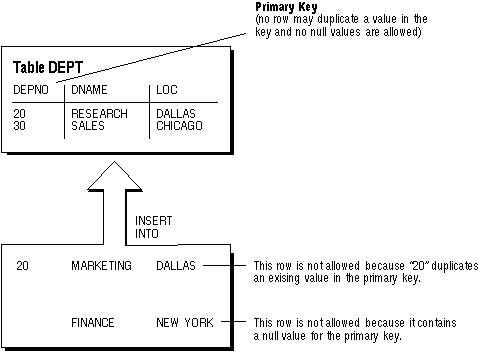
Figure 7 - 5. A Primary Key Constraint
PRIMARY KEY Constraints and Indexes
Oracle enforces all PRIMARY KEY constraints using indexes. In the previous example, the primary key constraint created for the DEPTNO column is enforced by
- the implicit creation of a unique index on that column
Because Oracle enforces primary key constraints using indexes, composite primary key constraints are limited to 16 columns, which is the same limitation imposed on composite indexes. The name of the index is the same as the name of the constraint. Also, you can specify the storage options for the index by including the ENABLE clause in the CREATE TABLE or ALTER TABLE statement used to create the constraint.
Referential Integrity and FOREIGN KEY (Referential) Integrity Constraints
Because tables of a relational database can be related by common columns, the rules that govern the relationship of the columns must be maintained. Referential integrity rules guarantee that these relationships are preserved.
There are several terms associated with referential integrity constraints:
A referential integrity constraint requires that for each row of a table, the value in the foreign key matches a value in a parent key.
Figure 7 - 6 illustrates the above terms.
Figure 7 - 6 shows a foreign key defined on the DEPTNO column of the EMP table. It guarantees that every value in this column must match a value in the primary key of the DEPT table (the DEPTNO column). Therefore, no erroneous department numbers can exist in the DEPTNO column of the EMP table.
Foreign keys can be comprised of multiple columns. However, a composite foreign key must reference a composite primary or unique key with the same number of columns and datatypes. Because composite primary and unique keys are limited to 16 columns, a composite foreign key is also limited to 16 columns.
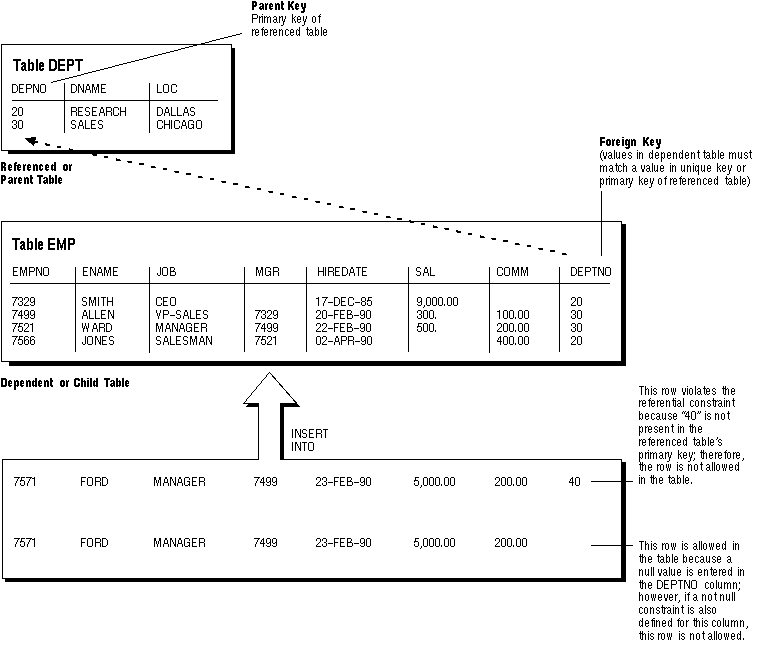
Figure 7 - 6. Referential Integrity Constraints
Self-Referential Integrity Constraints
Another type of referential integrity constraint, shown in Figure 7 - 7, is called a self-referential integrity constraint. This type of foreign key references a parent key of the same table. In the example below, you define the referential integrity constraint so that every value in the MGR column of the EMP table corresponds to a value that currently exists in the EMPNO column of the same table (that is, every manager must also be an employee). This integrity constraint eliminates the possibility of erroneous employee numbers in the MGR column.
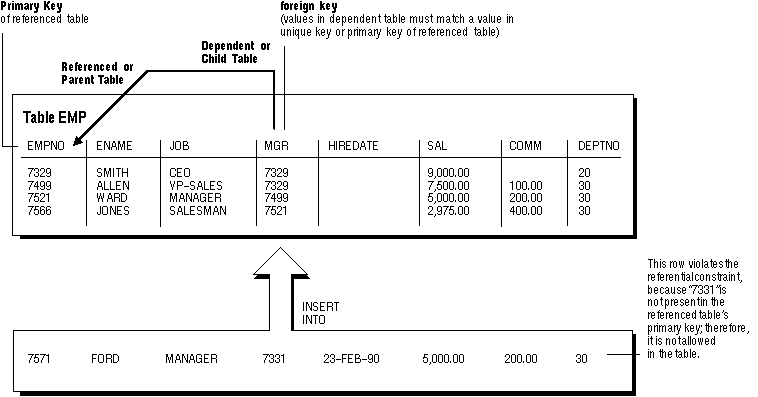
Figure 7 - 7. Single Table Referential Constraints
Nulls and Foreign Keys
The relational model permits foreign keys to be a value of the referenced primary or unique key, or null. There are several possible interpretations of this basic rule of the relational model when composite (multicolumn) foreign keys are involved.
The ANSI/ISO SQL92 (entry-level) standard permits a composite foreign key to contain any value in its non-null columns if any other column is null, even if those non-null values are not found in the referenced key. By using other constraints (for example, NOT NULL and CHECK constraints), you can alter the treatment of partially null foreign keys from this default treatment.
A composite foreign key can be all null, all non-null, or partially null. The following terms define three alternative matching rules for composite foreign keys:
| match full | Partially null foreign keys are not permitted. Either all components of the foreign key must be null, or the combination of values contained in the foreign key must appear as the primary or unique key value of a single row of the referenced table. |
| match partial | Partially null composite foreign keys are permitted. Either all components of the foreign key must be null, or the combination of non-null values contained in the foreign key must appear in the corresponding portion of the primary or unique key value of a single row in the referenced table. |
| match none | Partially null composite foreign keys are permitted. If any column of a composite foreign key is null, then the non-null portions of the key do not have to match any corresponding portion of a parent key. |
Actions Defined by Referential Integrity Constraints
Referential integrity constraints also specify particular actions that are performed on the dependent rows in a child table if a referenced parent key value is modified. The referential actions supported by the FOREIGN KEY integrity constraints of Oracle include UPDATE and DELETE RESTRICT, and DELETE CASCADE.
Note: Other referential actions not supported by FOREIGN KEY integrity constraints of Oracle can be enforced using database triggers. See Chapter 15, "Database Triggers," for more information regarding database triggers.
Update and Delete Restrict The restrict action specifies that referenced key values cannot be updated or deleted if the resulting data would violate a referential integrity constraint. For example, if a primary key value is referenced by a value in the foreign key, the referenced primary key value cannot be deleted because of the dependent data.
Delete Cascade The delete cascade action specifies that when rows containing referenced key values are deleted, all rows in child tables with dependent foreign key values are also deleted. Therefore, the delete cascades. For example, if a row in a parent table is deleted, and this row's primary key value is referenced by one or more foreign key values in a child table, the rows in the child table that reference the primary key value are also deleted from the child table.
DML Restrictions with Respect to Referential Actions Table 7 - 1 outlines the DML statements allowed by the different referential actions on the primary/unique key values in the parent table, and the foreign key values in the child table.
| DML Statement
| Issued Against Parent Table
| Issued Against Child Table
|
| INSERT
| Always OK if parent key value is unique.
| OK only if the foreign key value exists in the parent key or is partially or all null.
|
| UPDATE Restrict
| Allowed if the statement does not leave any rows in the child table without a referenced parent key value.
| Allowed if the new foreign key value still references a referenced key value.
|
| DELETE Restrict
| Allowed if no rows in the child table reference the parent key value.
| Always OK.
|
| DELETE Cascade
| Always OK.
| Always OK.
|
Table 7 - 1. DML Statements Allowed by Update and Delete Restrict
CHECK Integrity Constraints
A CHECK integrity constraint on a column or set of columns requires that a specified condition be true or unknown for every row of the table. If a DML statement is issued so that the condition of the CHECK constraint evaluates to false, the statement is rolled back.
The Check Condition
CHECK constraints allow you to enforce very specific or sophisticated integrity rules with the specification of a check condition. The condition of a CHECK constraint has some limitations, including that the condition must be a Boolean expression evaluated using the values in the row being inserted or updated, and cannot contain subqueries, sequences, the SYSDATE, UID, USER, or USERENV SQL functions, or the pseudocolumns LEVEL or ROWNUM.
In evaluating CHECK constraints that contain string literals or SQL functions with NLS parameters as arguments (such as TO_CHAR, TO_DATE, and TO_NUMBER), Oracle uses the database's NLS settings by default. You can override the defaults by specifying NLS parameters explicitly in such functions within the CHECK constraint definition. (For more information on NLS features, see Oracle7 Server Reference.)
Multiple CHECK Constraints
A single column can have multiple CHECK constraints that reference the column in its definition. There is no limit to the number of CHECK constraints that you can define on a column.


























